How To Change My Nat Type To Open
NAT - Network Address Translation
Introduction
Network Address Translation more often than not involves "re-writing the source and/or destination addresses of IP packets as they pass through a router or firewall" (from http://en.wikipedia.org/wiki/Network_Address_Translation)
This tutorial should explain what Network Accost Translation is about, what to apply it for and how to configure it under Linux (or more by and large Unix-derivates). This introduction does not merits to be complete or roofing all details, its main purpose is to provide the reader a feeling for what is possible and meaningful in modern estimator networks and what is not.
Showtime of all the structure of an IP-parcel will be considered. Subsequently a brusk overview of the possibilities of the (Linux-)kernel I volition jump right into the main area of application of NAT, namely the connection of a private subnet to the internet using a router (in our instance a linux machine with iptables). After that I would like to present some further possibilities like redirection or how to circumvent restrictive proxies. Still, I do non merits my presented solutions to be the most intelligent, most powerful or the most ingenious ones, they shall rather be understood every bit a proof of concept.
Packets within a network
Before we start to manipulate packets nosotros accept to have at look at their main attributes. I will restrict my considerations to IP-packets using TCP/UDP for the transport layer since these are the about common ones.
A detailled clarification of the structure of IP-packets can be found at various locations, e.g. IPv4 at Wikipedia. Our principal focus will be on the two fields Source Accost and Destination Address because they are containing - nomen est omen - the IP addresses of the source and the destination respectively.
Once an IP package is received the receiver has to assign the data to a process, which is the part of the transport layer, in our example TCP and UDP. Once again farther details can exist plant at various locations, e.thou. TCP at Wikipedia and UDP at Wikipedia and the linked resource there. For our purposes it is sufficient to know that each (networking) processes uses its ain port number(southward). For instance a http-Server uses port number 80, SSH uses port 22 and so on. The combination of IP-accost and port number is called socket and is unique. Therefore connections are uniquely defined by their endpoints (=sockets), a connection sends data from the clients socket to the server socket and vice versa, for case from the socket with IP 123.123.123.123, port 65432 to the socket with IP 112.112.112.112, Port eighty equally information technology may occur for a browser on 123.123.123.123 that connects to a http-server on 112.112.112.112. Server processes are commonly using standardised ports, so called 'well known ports', c.f. well known ports at IANA or well known ports at Wikipedia. A client usually uses a port from the upper port range (larger than 1023).
Linux and Netfilter
The Linux kernel usually posesses a packet filter framework called netfilter (Project home: netfilter.org). This framework enables a Linux motorcar with an appropriate number of network cards (interfaces) to become a router capable of NAT. We will use the command utility 'iptables' to create complex rules for modification and filtering of packets. The important rules regarding NAT are - non very surprising - found in the 'nat'-tabular array. This tabular array has three predefinded chains: PREROUTING, OUTPUT und POSTROUTING.
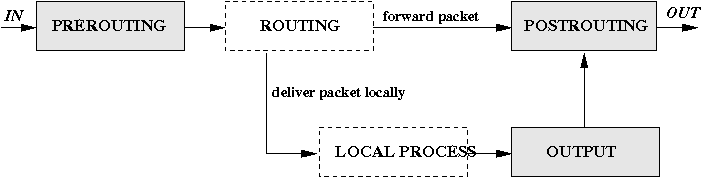
The chains PREROUTING und POSTROUTING are the most important ones. As the name implies, the PREROUTING chain is responsible for packets that merely arrived at the network interface. And then far no routing decision has taken place, therefore it is non nonetheless known whether the packet would be interpreted locally or whether it would be forwarded to another machine located at some other network interface. Afterwards the packet has passed the PREROUTING concatenation the routing decision is made. In case that the local automobile is the recipient, the package will be directed to the corresponding process and we practise not have to worry about NAT anymore. In case that the recipient is located in a (sub-)net located at a different network interface, the packet will exist forwarded to that interface, provided that the machine is configured to practice then. Just before our forwarded parcel leaves the machine it passes the POSTROUTING chain and and then leaves through the network interface. For locally generated packets there is a small divergence: Instead of passing through the PREROUTING concatenation it passes the OUTPUT chain and then moves on to the POSTROUTING concatenation.
Before nosotros get-go with our parcel manipulations nosotros have to enable the required features. To go all the needed functionality the commands (without '$>' at the beginning, lines starting with '#' are comments)
# # $>echo "1" > /proc/sys/cyberspace/ipv4/ip_forward# # # # $>modprobe ip_tables# # $>modprobe ip_conntrack# $>modprobe ip_conntrack_irc# $>modprobe ip_conntrack_ftp
should exist sufficient. In case of mistake messages information technology is likely that you do non have the routing features compiled into your kernel and should for example take a await at http://www.comptechdoc.org/os/linux/usersguide/linux_ugipmasq.html.
Instance: Connect a private subnet to the net using NAT
On the i hand nosotros know how IP packets look like, on the other hand we are ready to dispense packets under Linux (and other Unix derivates). Therefore we are gear up for our first application! The about popular question regarding NAT seems to be the one most sharing an internet connectedness for computers within a individual subnet. For this reason I want to start with this particular scenario.
An analogon: Several subtenants without own postal addresses
First we should consider the following accurate analogon which is hopefully much easier to understand: Let united states of america assume the following situation: at that place is a landlord with several subtenants. The postman has no idea near the subtenants und would reject every letter that is direct addressed to i of the subtenants. The landlord has several pigeon holes that can exist used for addressing. The subtenants have the possibility to place their letters in a postbox at the landlord's office who will and then take the letters to the post office. The question at present is: How can all the subtenants fully participate at any kind of mail correspondence (i.eastward. ship and receive messages)?
1 solution for this given trouble is the post-obit: The landlord takes the letters sent by the subtenants, assigns each subtenant a pigeon hole and then replaces the subtenants accost (which is in some sense invalid since the postman would reject any answers) by the landlord'southward own address including the pigeon hole number. The receipient of such a letter will and then send the reply back to the landlord including the pigeon hole number and then the landlord could easily paw over (after he has replaced his address by the subtenant's address so that the subtenant does not recognise this 'cheat') the letter to the matched subtenant. This solution is optimal in the sense that information technology is fully transparent for the subtenants, none of them would ever notice the postman not existence capable of sending letters direct to the subtenants!
From the subtenant problem to the computer world
NAT simply works like to the subtenant problem mentioned above. Every subtenant family represents an IP address in the local net, every subtenant family fellow member represents a port number, the landlords represents a router and the recipient acts every bit an arbitrary computer in the internet. Consequently a socket tin exist seen as a combination of address and pigeon hole or subtenant family und a member of that family. Let us recapitulate: The process of communication is every bit follows:
- The subtenants accept to put their letters into the postbox at the landlord'due south office
- The landlord replaces the sender'southward address past his own including the pigeon hole number
- In one case he gets a reply the landlord has to replace his address (including the pigeon hole number) with the corresponding subtenant'southward accost.
Actually the state of affairs in the local cyberspace is near the same:
- All computers inside the local net ('clients') send their packets with the receipient's socket to the router (this is actually realised by setting the router as standard gateway at the client, the delivery is so handled using Ethernet or any other lower level protocol).
- The router replaces the sender'south socket by an ain, unused socket.
- Replies to this specific socket volition exist forwarded to the appropriate computer in the local net, replacing the receipients accost (the router's socket) by the clients socket.
We volition presume that the standard gateway is ready properly at each client. All that is left is to configure the router. Fortunately the netfilter framework automatically adds to each dominion its changed dominion, therefore we but have to set i explicit dominion. Usually the decision for one of these two rules is made past taking the ane with the lower level of undetermination. For example, the dominion 'Replace the sender's accost for all packets from the local subnet' is much easier than 'if a customer has sent something to a server, then replace the receipient in the server's response by something'. As a rule of thumb can be used that the dominion that is executed first is the one that is set explicitly in the kernel.
How to set rules
All we want to have is the following: packets arriving from the local internet with a receipient'due south IP address somewhere in the internet have to exist modified such that the sender'due south address is equal to the router's accost. For further control examples allow us assume that the first interface 'eth0' is connected to the local cyberspace and that the router is connected to the internet via the 2nd interface 'eth1'. The command for a shared internet connection then simply is:
# $> iptables -t nat -A POSTROUTING -o eth1 -j MASQUERADE This command can be explained in the following way:
| iptables: | the command line utility for configuring the kernel | |
| -t nat | select table "nat" for configuration of NAT rules. | |
| -A POSTROUTING | Append a rule to the POSTROUTING chain (-A stands for "append"). | |
| -o eth1 | this rule is valid for packets that go out on the second network interface (-o stands for "output") | |
| -j MASQUERADE | the action that should take identify is to 'masquerade' packets, i.due east. replacing the sender's address past the router's accost. |
Some further comments on the above command instruction: packets generated past the router itself are masked likewise because they pass the POSTROUTING chain too! (see illustration further above) However, since the kernel tries to keep the source ports unchanged and processes running on the router acquire free ports just, locally generated packets commonly remain unchanged, although the rule is executed. The output interface tin can exist of any blazon, ISDN or DSL interfaces are as well possible (often 'ppp0' or 'ippp0'). A quick overview of all bachelor network interfaces gives
Disadvantages of using NAT
Local computers tin admission the internet, but there are still some restrictions left. A figurer located in the internet is not able to establish a connection to a local calculator, all he can practise is address (a port of) the router and hope for the all-time. Usually the addressed port is currently not used and hence the packet will be rejected. Even if the port is currently used by a local machine the bundle might exist forwarded only will then unremarkably be rejected since the computer is already communicating with a different calculator. Establishing connections from the internet to ane of the local computers is therefore nearly impossible. For regular services it is possible to statically map ports on the router to sockets in the local internet, for example one can configure the router to forrad packets arriving at port 80 to a HTTP-server located in the local internet. Very often this is needed for playing online games, especially if you desire to host games.
A closer look at iptables
At present that we have mastered our first claiming it is time to accept a closer look (or 2) at the possibilites of iptables. An iptables-call has the following pattern:
# iptables [-t table] command [match pattern] [action] For NAT we always have to cull the nat-table. A command might need further options, for example a blueprint and an activeness to perform in instance the pattern matches.
Choosing a table
All our commands regarding NAT will commencement similar this:
# # iptables -t nat [...] This selects the nat-table. At that place are two other tables, namely mangle und filter, just those are not used for NAT and therefore I mention them for completeness only. Since the default table is filter nosotros have to select the nat tabular array every time once again.
Commands
The near important commands are the post-obit: (further patterns and actions once again abbreviated with [...])
# # # $>iptables -t nat -A concatenation [...]# $>iptables -t nat -L# $>iptables -t nat -D chain myindex# $>iptables -t nat -F chain
For a full list of all possible commands I recommend the manual pages of iptables. To view them, simply type
and quit by typing 'q'.
Choosing match patterns
To manipulate specific packets we have to use appropriate match patterns, therefore there a numerous options to specify them. I will present the virtually popular ones to clarify their usage. All available match patterns can exist plant in the transmission pages of iptables.
# # # # $>iptables -t nat -A POSTROUTING -p tcp -south 192.168.ane.2 [...]# $>iptables -t nat -A POSTROUTING -p udp -d 192.168.1.2 [...]# $>iptables -t nat -A PREROUTING -s 192.168.0.0/16 -i eth0 [...]# $>iptables -t nat -A PREROUTING -p ! tcp -southward ! 192.168.1.ii [...]# $>iptables -t nat -A POSTROUTING -o eth1 [...]# # # $>iptables -t nat -A POSTROUTING -p tcp -s 192.168.ane.two \--sport 12345:12356 -d 123.123.123.123 --dport 22 [...]
For most of the switches there exists a long form, eastward.g. --source instead of -south. Using them makes the whole instruction longer but more than readable, especially if y'all are new to iptables.
Actions for matched packets
We are already able to select desired packets, all that is left is an appropriate action. For the nat-table just the deportment SNAT, MASQUERADE, DNAT and REDIRECT, all of them with preceeding '-j', are meaningful. Their exact pregnant will be explained in the subsequent section.
# # # $>iptables [...] -j SNAT --to-source 123.123.123.123# $>iptables [...] -j MASQUERADE# $>iptables [...] -j DNAT --to-destination 123.123.123.123:22# $>iptables [...] -j REDIRECT --to-ports 8080
Explaination of possible actions
Now most of the options of iptables are explained and information technology is time to have a closer await at the four possible actions:
Source-NAT (SNAT) - Alter sender statically
In our previous case of connecting a local internet to the cyberspace we already used Source NAT (curt: SNAT). As the proper noun implies the sender'south address is inverse statically. The reason for choosing MASQUERADE in the previous example anyway has the following reason: For SNAT 1 has to specify the new source-IP explicitly. For routers with a static IP address SNAT is the all-time choice because it is faster than MASQUERADE which has to check the electric current IP address of the outgoing network interface at every packet. Since SNAT is only meaningful for packets leaving the router it is used within the POSTROUTING concatenation simply.
# --to-source <ipaddr>[-<ipaddr>][:port-port] MASQUERADE - Change sender to router's IP-Adress
Using the MASQUERADE target every packet receives the IP of the router's outgoing interface. The advantage over SNAT is that dynamically assigned IP addresses from the provider practice not affect the rule, there is no need to adopt the dominion. For ordinary SNAT yous would have to change the rule every time the IP of the approachable interface changes. As for SNAT, MASQUERADE is meaningful within the POSTROUTING-chain merely. Unlike SNAT, MASQUERADE does not offering further options.
Destination-NAT (DNAT) - Changing the receipient
If yous want to alter the receipient of a packet, Destination NAT (DNAT) is your choice! DNAT tin exist used for servers running behind a firewall. Manifestly the receipient has to be changed earlier any routing decisions are made, therefore DNAT is meaningful within the PREROUTING chain and the OUTPUT chain (for locally generated packets) only.
# --to-destination <ipaddr>[-<ipaddr>][:port-port] REDIRECT - Redirect packets to local machine
A special example of DNAT is REDIRECT. Packets are redirected to a local port of the router, enabling for example transparent proxying. As for DNAT, REDIRECT acts within the PREROUTING and the OUTPUT chain respectively.
# --to-ports <port>[-<port>] Applications
Probably you have been confused by the cryptic instructions used in the first example (connecting a local net to the internet). Now, subsequently some explanations, the instructions are hopefully a picayune flake clearer than earlier. The question might have changed from 'How tin someone construct such cryptic instructions' to 'Okay, and what can I practice with all these cryptic instructions?'. This department tries to give you lot some ideas on how to use NAT. The range of applications is moreless unlimited, still I will effort to cover the most spread use cases.
Transparent Proxying
Let united states of america assume that we accept a local cyberspace connected to the internet using NAT. To keep the traffic low we would like to run a HTTP-proxy on port 8080 of the local network interface handling all of the http-traffic.
The first solution that comes in mind is to 'motivate' each user (i.due east. do information technology on your own) to configure their browser to use the proxy server and afterwards block all outgoing traffic to port lxxx. This might be a satisfactory solution for small networks but does not calibration for large networks, because you would have to accept intendance on every single client! (At to the lowest degree yous avoid the disadvantages of transparent proxying...)
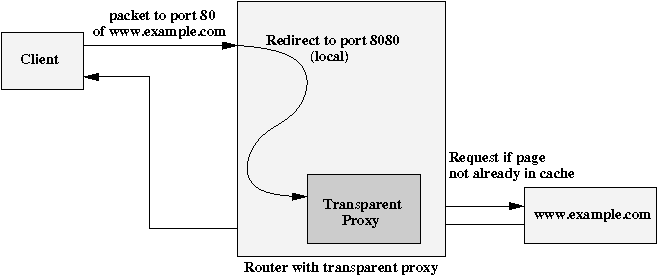
With NAT we take some other possibility: All incoming packets going to port 80 will exist redirected to port 8080. The command is:
# # $> iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 \ -j REDIRECT --to-ports 8080 Of class a HTTP-Proxy at port 8080 needs to exist upward and running. Possibly some special configurations (or even a special compilation) are needed for your proxy server in lodge to support transparent proxying. Disadvantages of transparent proxying are the higher CPU load (specially for really large networks) and some problems with old or very simple browsers.
Assist! I am behind a restrictive firewall!
Before nosotros start I have to identify a alert:
Everybody has to check on his or her own, whether the post-obit steps violate any existing usage conditions, Before he or she uses 1 of the presented techniques! Usage of the following commands are at your own risk; I am non responsible for amercement or fines that result from an inappropriate employ of the post-obit commands and techniques!
Although you may not expect information technology, but NAT can even aid you in such a case! Allow us assume that only a few ports can be reached from your local network. Get-go of all 1 has to observe these open up ports. Ane wide spread utility to use is nmap: (please scan your ain computers but, scanning unknown computers tin be interpreted as a first footstep to intrusion!)
# # $> nmap www.example.com The output volition display various ports, almost of them volition be in country 'closed' (no service at that port), others volition be in country 'filtered' (no connexion to that port), perhaps some are in state 'open' (service running). Let the states assume all ports beneath 5000 are closed, except port 80, but there are ports starting at 5000 that tin be reached. To go a connection to any port beneath 5000 to an arbitrary machine i needs a (Linux-) machine that is located outside the firewall (no matter where equally long as it can exist reached and is non itself restricted by a firewall), that can exist accessed and that supports NAT (iptables).
Beginning of all we have to gain access to that machine (suppose IP 111.111.111.111) outside the firewall. We apply whatsoever workstation outside the firewall to institute a SSH connection to 111.111.111.111. Then we event the command
# $> iptables -t nat -A PREROUTING -p tcp --dport 5000 -j REDIRECT --to-ports 22 Now we can return to our machine behind the restrictive firewall and can access 111.111.111.111 via SSH on port 5000. Alternatively you can configure your SSH-daemon to run on port 5000. However, at present y'all are able to configure the remote machine appropriately. To connect to port 110 (POP3) on machine 123.123.123.123, upshot the command
# $>iptables -t nat -A PREROUTING -p tcp --dport 5001 \ -j DNAT --to-destination 123.123.123.123:110# $>iptables -t nat -A POSTROUTING -p tcp --dport 110 \ -j MASQUERADE
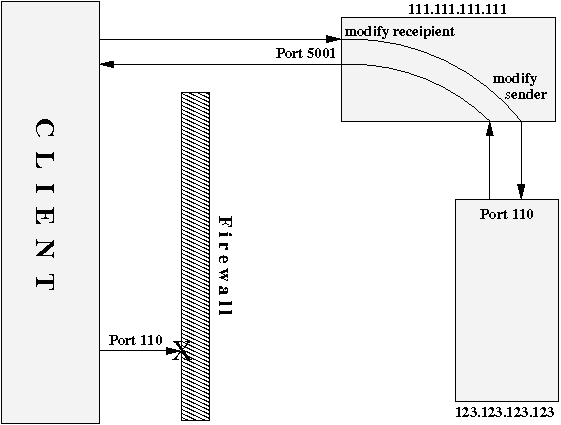
Instead of the final MASQUERADE command SNAT is possible as well (-j SNAT --to-source 111.111.111.111), but since we are the only user of that connection this does not matter, therefore I chose MASQUERADE because information technology is shorter and easier to use.
We can connect to all other ports in exactly the same style as long as nosotros accept enough open ports. Even secure connections (like IMAPS) can exist redirected in that way, warnings regarding the security certificate have to exist ignored (as long as we know what we are doing!). For the POP3-connection from above you lot still take to configure your mail customer accordingly, your server for mails would then exist 111.111.111.111, port 5001.
If our 'provider' runs a proxy for connections to port 80 (i.e. the provider uses a transparent proxy) and monitors the content and nosotros do not agree with that, then NAT tin help us once again. Bold that proxy avoidance is not prohibited, we tin can set up a proxy (configured for transparent proxying) at 111.111.111.111, port 5002. After that y'all enter on your local motorcar the following command:
# $> iptables -t nat -A OUTPUT -p tcp --dport 80 \ -j DNAT --to-destination 111.111.111.111:5002 In that way you have successfully circumvented the provider's proxy! (In my view it is very fancy to circumvent a transparent proxy using a transparent proxy! :-) ) Alternatively yous can once again configure your browser by hand to use your new proxy, but this may nevertheless pb to some troubles with other programs. However, configuring your browser by hand would at to the lowest degree avoid the disadvantages of transparent proxying.
To close this awarding I want to recapitulate our steps: First we find an open up port for a SSH-connectedness. Then we statically redirect the other open ports to the desired destinations (normally one is not using that many not-HTTP-servers). If 1 manages to do this redirection dynamically, then ii open TCP ports (ane for SSH) and one open UDP port are sufficient to connect to virtually every port at every motorcar, the only disadvantage then would be that yous tin accept only 1 connection at a time (per protocol).
Running a Server backside a NAT-router
For servers running backside a NAT-router boosted steps are needed since at starting time you cannot connect from outside to the server. Let united states assume that nosotros have a HTTP-server with IP 192.168.1.2 and our router has the IP accost 192.168.1.ane and is connected to the internet over its second network interface with IP 123.123.123.123. To attain the HTTP-server from exterior, type
# $> iptables -t nat -A PREROUTING -p tcp -i eth1 --dport lxxx -j DNAT --to 192.168.1.2 and you are done. Now you are able to access the HTTP-server from outside using the IP 123.123.123.123.
Related articles
Similar topics tin be found nether:
- http://iptables-tutorial.frozentux.net/iptables-tutorial.html : Very comprehensive source of informations near iptables.
- http://www.faqs.org/docs/Linux-mini/TransparentProxy.html : Dealing extensively with transparent proxying.
- http://www.barryodonovan.com/publications/lg/108/ : Further abilities of the netfilter Framework by use of extensions.
Closing words, acknowledgement and so on
The netfilter framework is very powerful but however quite easy to configure one time you are used to the syntax. Many tasks tin exist achieved and although at first sight the commands are cryptic, they dismantle after some practise to very well structured patterns that allow quick and unproblematic administration.
I would like to give thanks every tough reader who managed it up to these lines :-) Further I give thanks my laptop running SUSE 10.1 that hasn't crashed while writing this commodity.
Since my mother tongue is non English language, I am very happy about all hints on how to meliorate certain words/sentences/passages! Equally for the technical part, experience free to employ the comment module below or write me an E-mail (use my contact accost or  ) if y'all have any proposals, wishes or complaints.
) if y'all have any proposals, wishes or complaints.
Comments:
Very helpful
Good morning from Espana. I want to contact you because I took some iptables rules from your blog and use it on my blog: https://freelifeblog.wordpress.com/2013/09/19/iptables-reglas-contra-fuerza-bruta-escaneos/
Rules I have used from you have references in your post: http://www.karlrupp.internet/en/computer/nat_tutorial
Sorry for not enquire you earlier to mail. If y'all want I can delete entire mail service or snippet where I use those rules. Anyway I accept reference your web log.
Sorry for advise you so later, but I couldn´t practice it earlier.
Kind regards
Very useful article and very nicely written.
Diagnostics help eastward.g. log messages could be useful for beginners to iptables.
Bro, u'r the homo!
its helpful
Best article on NAT on Net..thumbs man !!!
Awesome caption
Not bad Read!
wonderful work congrats!
Very very simple and very very very proficient
You must be a good teacher. Fifty-fifty though it is fully understood in the get-go reading , i think it is the best tutorial available in the net. I wish you could help me to solve my problem of FTP-Transparent proxy trouble. Thank you a lot
In Connect a LAN to the internet, in the case you drop forwarding in your default policy :
iptables -P Forward Drib
statefully :
iptables -A Forward -one thousand state --state RELATED,ESTABLISHED -j Accept
practise non forget in add-on to masquerading to authorize forwarding from your LAN. Say 192.168.0.0/24 is the LAN of your host and 192.168.1.0/24 the LAN you want to connect to the Spider web, and so :
iptables -I FORWARD i -southward 192.168.1.0/24 ! -d 192.168.0.0/24 -j ACCEPT
thank you a lot for this great commodity
excellent commodity with skilful instructorship
Cheers very much for this wonderful explanation
sir i am raj,
(case)
Ethernet ane: i assign this ip
my internet ip is : 111.119.81.194
Subnet mask is : 255.255.255.252
Default Gateway is : 111.115.81.193
Ethernet 2 : I assign this ip
my Lan IP is : 192.168.0.12
Subnet mask is : 255.255.255.0
Default Gateway is : 0.0.0.0
Usable Range IP is: 111.115.132.104/29
IP ane : 111.115.132.106 this lan ip give to me my internet access provider providers
IP ane : 111.115.132.107
IP 1 : 111.115.132.108
IP 1 : 111.115.132.109
IP one : 111.115.132.110
gateway ip : 111.115.132.105
Circulate ip : 111.115.132.111
How to i nat usable range ip to my individual ip
111.115.132.106 nat 192.168.0.211
111.115.132.107 nat 192.168.0.212
111.115.132.108 nat 192.168.0.213
111.115.132.109 nat 192.168.0.214
111.115.132.110 nat 192.168.0.215
this is my ip tables configuration
# Generated by iptables-save v1.iv.7 on Tue Oct 30 16:30:47 2012
*nat
:PREROUTING Have [178:11422]
:POSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A PREROUTING -i eth1 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.0.12:3128
-A PREROUTING -i eth1 -p tcp -grand tcp --dport 443 -j DNAT --to-destination 192.168.0.12:3128
-A PREROUTING -d 111.115.132.106/32 -p tcp -one thousand tcp --dport 80 -j DNAT --to-destination 192.168.0.211
-A POSTROUTING -s 192.168.0.0/24 -o eth0 -j MASQUERADE
COMMIT
# Completed on Tue Oct xxx xvi:30:47 2012
# Generated past iptables-save v1.4.vii on Tue Oct thirty sixteen:30:47 2012
*filter
:INPUT Take [0:0]
:Forrad Accept [0:0]
:OUTPUT ACCEPT [6605:832098]
-A INPUT -one thousand country --country RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j Take
-A INPUT -i lo -j Have
-A INPUT -p tcp -m land --state NEW -m tcp --dport 22 -j Have
-A INPUT -p tcp -chiliad tcp --dport 3128 -j ACCEPT
-A INPUT -j Reject --reject-with icmp-host-prohibited
COMMIT
# Completed on Tue Oct 30 sixteen:30:47 2012
But this iptables did not working for nat ip translation
great article. thank you a lot. :)
i want iptables commands more than and more ..i could not empathise iptables please assist me....
Its perfect !!!!
Our confusion over iptables rules got cleared every-fourth dimension nosotros referred this post :)
Very useful and articulate :)
best on the internet by far
Splendid article, Best on the net.
the all-time iptables tutorial i ever founded...
u explained the basics very well,thanks
very skilful, thanks
Very Helpful Doc for configuring IPTABLES.
www.rhcsolutions.info/rhc
thank you, very good article
very very proficient article
it so helpful for me
Great Article .
Great commodity. Many thanks. Explains how NAT works, just what I needed.
tin can u send me on mail service how configure nat in linux
Very nicely explained. Cracking work!!
i want hole configuration of linux proxy server
Source: https://www.karlrupp.net/en/computer/nat_tutorial
Posted by: thorntonxvier1937.blogspot.com


0 Response to "How To Change My Nat Type To Open"
Post a Comment